runfallguys.exe已停止工作解决方法(winlogon.exe怎么修复)
2023-06-09 11:46:34 阅读( 5412)
这只鸽子提示:中招后,贴日志求助的日子即将结束!做好系统基础安全防护是每个用户的当务之急。
这只鸽子提示,被招募后发日志求助的日子就要结束了!做好系统的基础安全防护,是每个用户的当务之急。“基本安全保护”不仅仅是打补丁这么简单。还需要熟悉一两款性能良好的安全软件的使用。否则,在变戏法之后,
你自己操心就好!
这只鸽子的密钥是c:\ windows \ winlogon.dll。如果您试图阻止这个dll的加载和运行,所有的pigeon文件都可以在图1中看到。
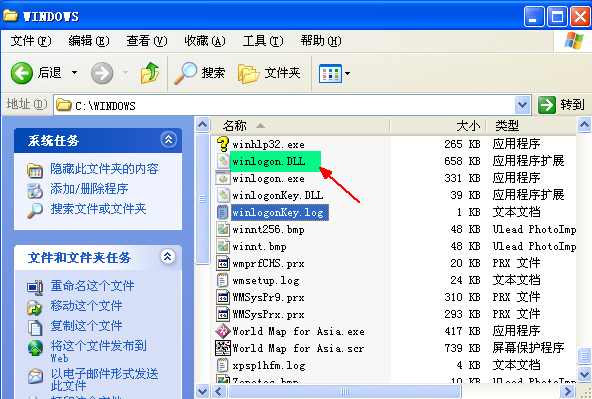
这只鸽子的钥匙是这个c:\ Windows \ winlogon.dll。
如果用SSM阻止c:\windows\winlogon.dll加载运行,那么这只鸽子的所有文件都是可见的。
这是一只被拴在Movgear.exe的灰鸽子(来自Movgear.exe的样本距离安全地带12公里)。winlogon.exe的MD5值为2 de 9 f 62 C2 b 405 e 16 CB 66773747 cf 02d。
1.从Movgear.exe提取winlogon.exe并植入系统后,在自动运行、劫持和SREng日志中没有发现异常。
winlogon.exe公布的文件有:
1、c:\windows\winlogon.exe
2、c:\windows\winlogon.dll
3、c:\windows\winlogonKey.dll
这两个dll插入到IE浏览器进程中。
即使不打开ie浏览器,在冰剑的进程列表中仍然可以看到iexplore.exe。
C:\windows\winlogonKey.dll动态跟踪所有应用程序进程(一旦打开,立即插入。)
注意:即使显示隐藏文件,灰鸽发布的这三个文件也是WINDOWS资源管理器看不到的。只有用冰剑才能看到。
其次,注册表的变化包括:
1、在HKEY _ LOCAL _ MACHINE \ SYSTEM \ current control set \ Services
添加:winlogon.exe(指向c:\windows\winlogon.exe)
2、在HKEY _用户\。默认\软件\ Microsoft \ Internet Explorer \ Extensions \ cmd映射
添加:
'{92780B25-18CC-41C8-B9BE-3C9C571A8263}'=dword:00002002
'{DEDEB80D-FA35-45d9-9460-4983E5A8AFE6}'=dword:00002002
'{FB5F1910-F110-11d2-BB9E-00C04F795683}'=dword:00002001
3、在HKEY_USERS\.DEFAULT\Software\Microsoft\Internet Connection Wizard
添加:'Completed'=hex:01,00,00,00
4、在HKEY_USERS\.DEFAULT\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser
添加:
'ITBarLayout'=hex:11,00,00,00,5c,00,00,00,00,00,00,00,34,00,00,00,1f,00,00,00,56,\
00,00,00,01,00,00,00,20,07,00,00,a0,0f,00,00,05,00,00,00,62,05,\
00,00,26,00,00,00,02,00,00,00,21,07,00,00,a0,0f,00,00,04,00,00,\
00,21,01,00,00,a0,0f,00,00,03,00,00,00,20,03,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00
'{01E04581-4EEE-11D0-BFE9-00AA005B4383}'=hex:81,45,e0,01,ee,4e,d0,11,bf,e9,00,aa,00,5b,43,83,10,00,00,00,00,\
00,00,00,01,e0,32,f4,01,00,00,00
'{0E5CBF21-D15F-11D0-8301-00AA005B4383}'=hex:21,bf,5c,0e,5f,d1,d0,11,83,01,00,aa,00,5b,43,83,22,00,1c,00,08,\
00,00,00,06,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,4c,00,00,00,01,14,02,00,00,00,00,00,c0,00,00,00,00,00,00,\
46,81,00,00,00,10,00,00,00,a0,8f,ff,ba,9d,d4,c6,01,00,9e,02,bb,\
9d,d4,c6,01,a0,8f,ff,ba,9d,d4,c6,01,00,00,00,00,00,00,00,00,01,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,5d,01,14,00,1f,50,\
e0,4f,d0,20,ea,3a,69,10,a2,d8,08,00,2b,30,30,9d,19,00,2f,43,3a,\
5c,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,5c,\
00,31,00,00,00,00,00,3a,31,09,3c,10,00,44,4f,43,55,4d,45,7e,31,\
00,00,44,00,03,00,04,00,ef,be,3a,31,9c,36,2a,35,f7,29,14,00,00,\
00,44,00,6f,00,63,00,75,00,6d,00,65,00,6e,00,74,00,73,00,20,00,\
61,00,6e,00,64,00,20,00,53,00,65,00,74,00,74,00,69,00,6e,00,67,\
00,73,00,00,00,18,00,4c,00,31,00,00,00,00,00,2a,35,cb,2e,16,00,\
4e,45,54,57,4f,52,7e,31,00,00,34,00,03,00,04,00,ef,be,3a,31,11,\
39,2a,35,cb,2e,14,00,00,00,4e,00,65,00,74,00,77,00,6f,00,72,00,\
6b,00,53,00,65,00,72,00,76,00,69,00,63,00,65,00,00,00,18,00,56,\
00,31,00,00,00,00,00,2a,35,cb,2e,11,00,46,41,56,4f,52,49,7e,31,\
00,00,3e,00,03,00,04,00,ef,be,2a,35,cb,2e,2a,35,cb,2e,14,00,28,\
00,46,00,61,00,76,00,6f,00,72,00,69,00,74,00,65,00,73,00,00,00,\
40,73,68,65,6c,6c,33,32,2e,64,6c,6c,2c,2d,31,32,36,39,33,00,18,\
00,30,00,35,00,00,00,00,00,2a,35,f1,2e,10,00,fe,94,a5,63,00,00,\
1c,00,03,00,04,00,ef,be,2a,35,f1,2e,2a,35,f1,2e,14,00,00,00,fe,\
94,a5,63,00,00,14,00,00,00,60,00,00,00,03,00,00,a0,58,00,00,00,\
00,00,00,00,6c,69,6e,62,61,6f,68,65,00,00,00,00,00,00,00,00,1e,\
8c,63,4d,34,72,b3,48,8a,de,83,67,8f,38,be,10,b1,a9,fd,89,90,40,\
db,11,b2,29,00,d0,59,c0,b8,59,1e,8c,63,4d,34,72,b3,48,8a,de,83,\
67,8f,38,be,10,b1,a9,fd,89,90,40,db,11,b2,29,00,d0,59,c0,b8,59,\
00,00,00,00
5、在HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\CabinetState
添加:'Settings'=hex:0c,00,02,00,0a,01,ef,75,60,00,00,00
6、在HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\
添加:
{0055C089-8582-441B-A0BF-17B458C2A3A8}
{06849E9F-C8D7-4D59-B87D-784B7D6BE0B3}
{92780B25-18CC-41C8-B9BE-3C9C571A8263}
{AE7CD045-E861-484F-8273-0445EE161910}
{DEDEB80D-FA35-45D9-9460-4983E5A8AFE6}
{FB5F1910-F110-11D2-BB9E-00C04F795683}
7、在HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\MenuOrder\Favorites\链接
添加:'Order'=hex:08,00,00,00,02,00,00,00,0c,00,00,00,01,00,00,00,00,00,00,00
三、进行上述观察后,重启系统。
重启后,卡巴斯基报警(我的卡巴斯基为启动加载):发现灰鸽子。
但卡巴斯基仅仅将c:\windows\winlogon.dll删除;c:\windows\winlogon.exe和c:\windows\winlogonKey.dll卡巴斯基并不报毒。
汗!卡巴斯基越来越不争气了另外发现其winlogonKey.log文件。文件内容为:
#?4?74;
四、查杀流程:
1、打开注册表编辑器,展开HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
删除灰鸽子的服务项:winlogon.exe
2、重启系统。用IceSword找到并删除鸽子释放的那三个文件。
4、清理注册表(删除鸽子添加的注册表项)。
10月31日更新
查杀方法.
安全模式下操作.
删除文件
C:\Downloads
C:\WINDOWS\system32\AddrConfig.bin
C:\WINDOWS\system32\oobe\data
C:\WINDOWS\system32\wbem\ddes
C:\WINDOWS\system32\wbem\kbd101ab.dll
C:\WINDOWS\system32\wbem\SysOption.bin
C:\WINDOWS\system32\wbem\winlogon.exe
删除注册表
HKCR\CLSID\{881F6F06-4620-4070-AD05-BD77D4C56661}
HKCR\Interface\{468262B9-8400-4A49-B2E5-CE8550EB1347}
HKCR\TypeLib\{F63B08CD-3645-474F-8872-BA4293251FF9}\1.0
HKCR\VCFIWZDY32.VCFIWZDY
猜你喜欢
Guessyoulike